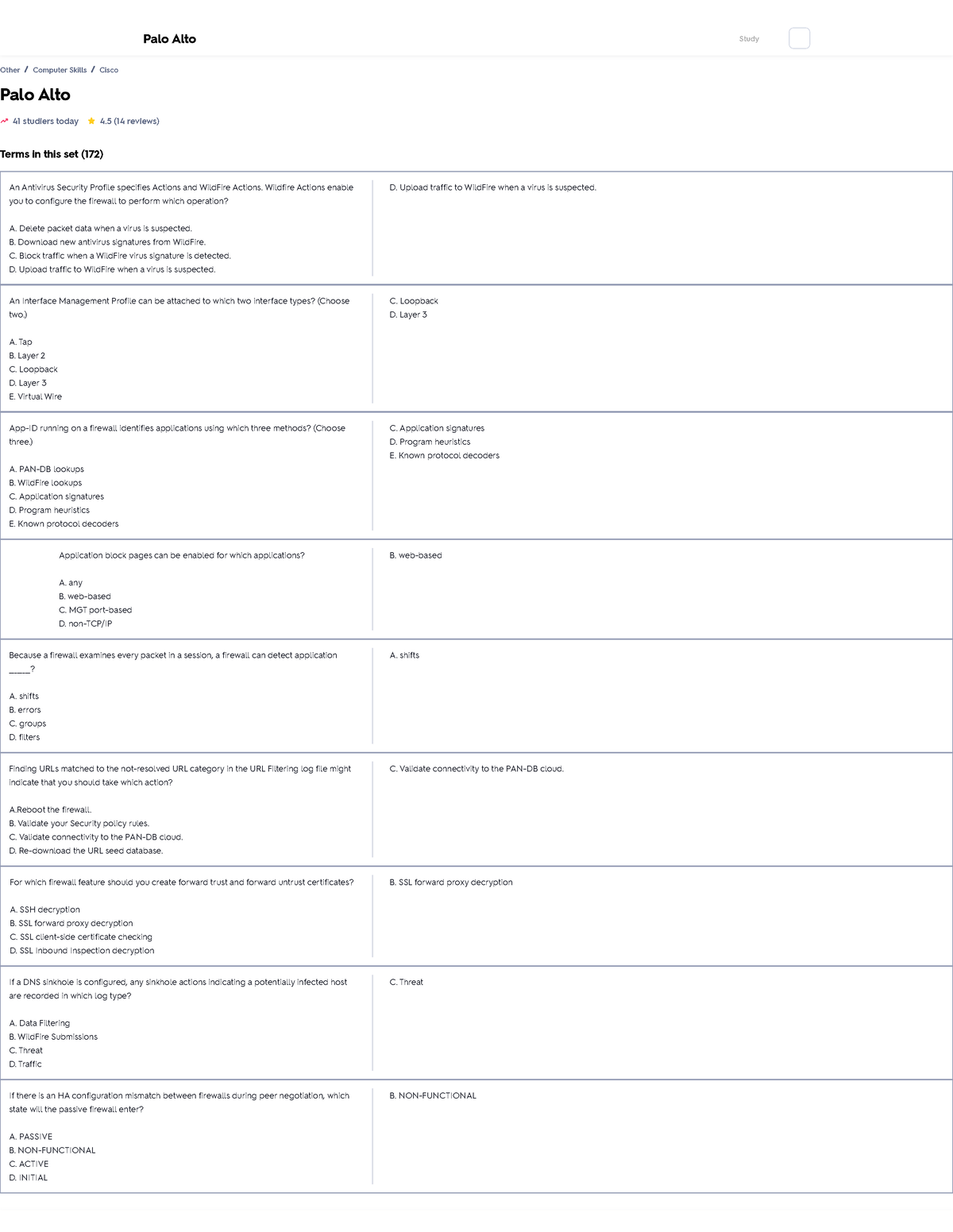
45 antivirus inspection is proxy based palo alto
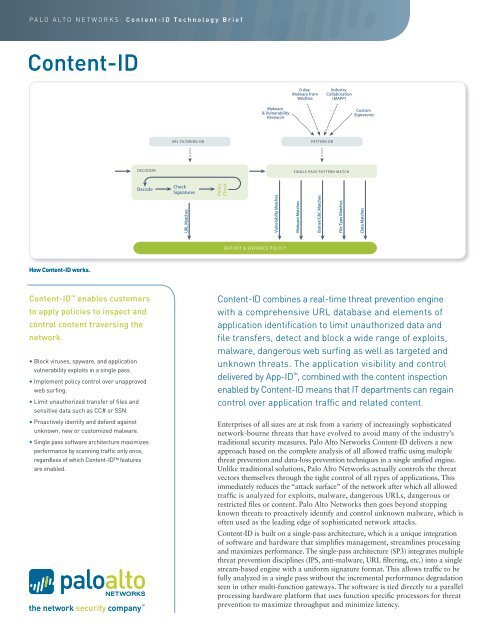
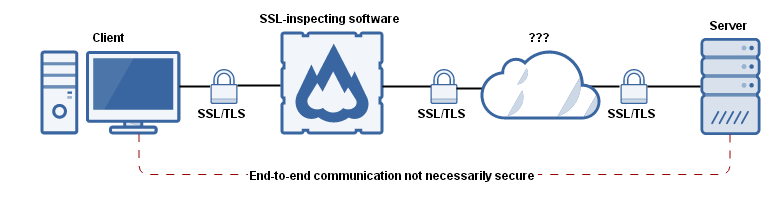
Why Proxy-Based Firewalls Are Not Enough - Palo Alto Networks Blog Proxy-based firewalls were never designed to deal with modern security threats and only inspect a limited number of protocols such as HTTP, HTTPS, FTP and DNS. This means that using only web proxies leads to significant blindspots in traffic and an inability to identify applications and threats on non-standard ports or across multiple protocols. PDF Palo Alto Networks v Proxies TechBrief May2012 Dempsey edit 1 PALO ALTO NETWORKS: Technology Brief ABOUT PROXY-BASED PRODUCTS Proxies (both firewall and caching) sit between the source and destination, intercepting traffic and inspecting it by terminating the application session, re-initiating the connection to the target destination.
HTTP/2 Inspection | Palo Alto Networks HTTP/2 Inspection. 07-09-2020 04:03 PM. HTTP/2 (also known as HTTP/2.0) is a revision of the HTTP network protocol. As browsers such as Chrome, Firefox, and Edge start to support HTTP/2, your Palo Alto Networks firewall will need to look into the HTTP/2 traffic to perform inspection. Starting with PAN-OS 9.0.0, HTTP/2 inspection is supported on ...
Antivirus inspection is proxy based palo alto
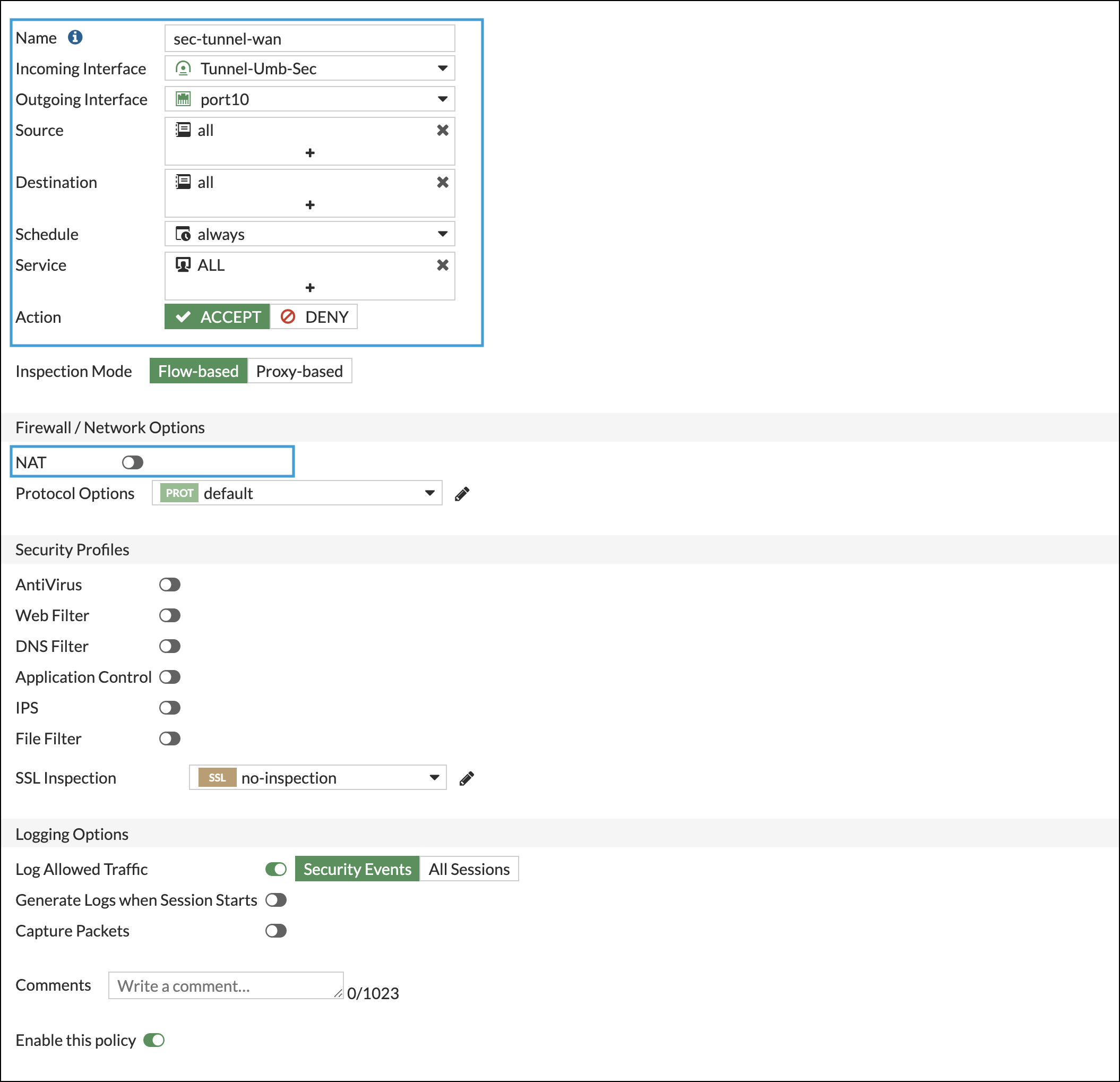
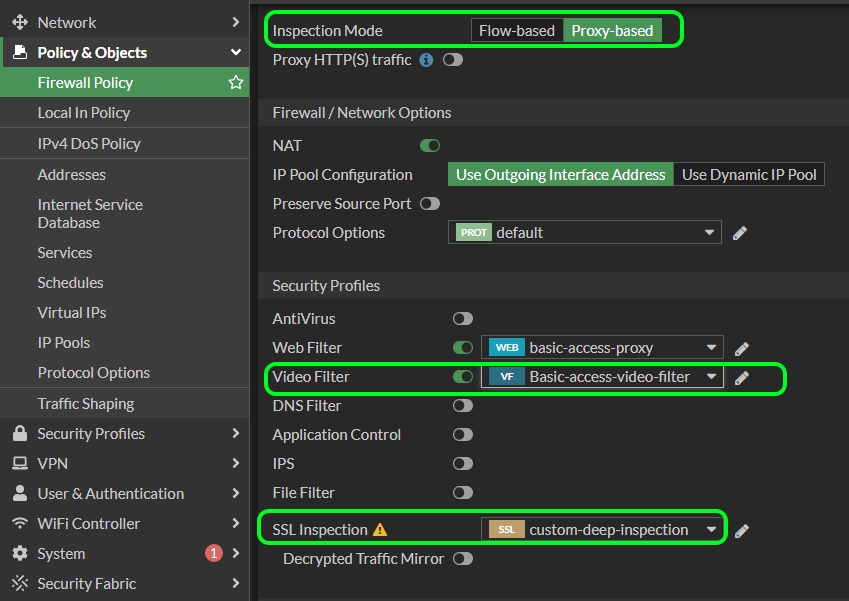
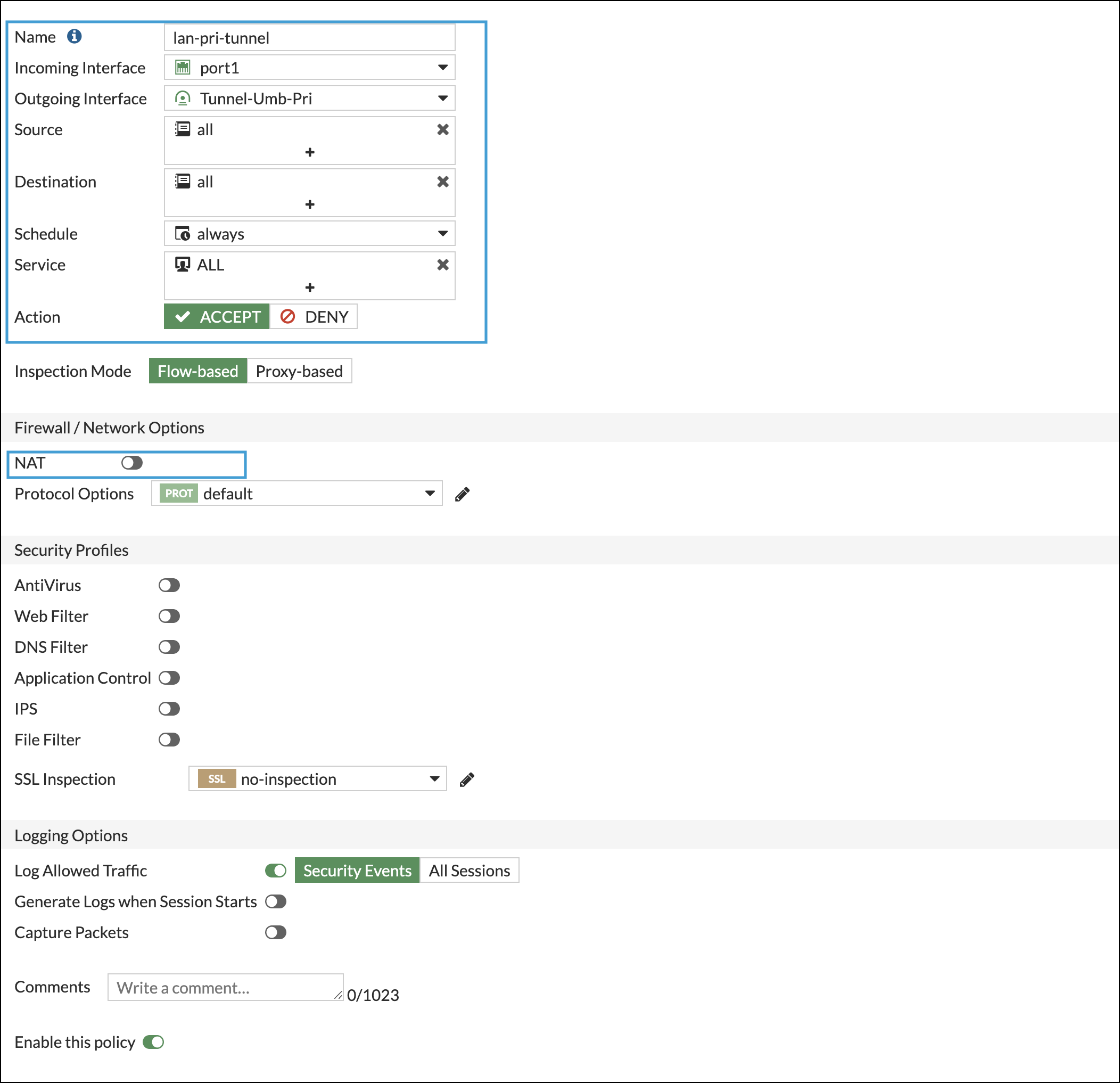
types of PA firewall inspection - Palo Alto Networks For example, the Fortigate firewall has 2 inspection modes, the base flow mode and the proxy mode, my question is The Palo Alto firewall, does it also have these types of inspection modes? 0 Likes Share Reply Go to solution MP18 Cyber Elite In response to o_hernandez Options 11-02-2019 08:26 PM Best Practices for Ransomware Prevention - Palo Alto Networks The Anti-Virus and Wildfire content contains a list of domains Palo Alto Networks has identified as being potentially associated with malicious traffic; network administrators can block DNS requests to these domains with this profile, or choose to sinkhole the traffic to an internal IP address they have configured for further analysis. Security Profile: Antivirus - Palo Alto Networks Antivirus profiles protect against viruses, worms, and trojans as well as spyware downloads. Using a stream-based malware prevention engine, which inspects traffic the moment the first packet is received, the Palo Alto Networks antivirus solution can provide protection for clients without significantly impacting the performance.
Antivirus inspection is proxy based palo alto. Is HTTP version 2 (HTTP/2) supported? - Palo Alto Networks With inbound inspection the traffic is identified as unknown-tcp. With forward proxy, if the client sends an ALPN extension with h2 then the firewall, as client, strips the ALPN extension in the crafted Client Hello to the server. As a result the connection is negotiated as HTTP/1.1. Additional Information What Is a Proxy Server - Palo Alto Networks Proxies and Secure Web Gateways Proxies are often implemented as part of a secure web gateway (SWG). This provides security inspection of HTTP and HTTPS web protocols along with URL filtering and malware prevention. Organizations can also use proxies instead of deploying agents on user devices. Palo Alto Networks - Network-based Malware Protection - NextGig Systems ... Palo Alto Networks next-generation firewalls allow organizations to first block unwanted applications with App-ID and then scan the allowed applications for malware. Questions? Call 1-805-277-2400 Broad-based protection against a range of malware. Best Practice Security Profiles - Palo Alto Networks DNS Security is enabled as part of both best practice Anti-Spyware profiles. This means that DNS queries to malicious domains are sinkholed to a Palo Alto Networks server IP address, so that you can easily identify infected hosts.
Security Profile: Antivirus - Palo Alto Networks Antivirus profiles protect against viruses, worms, and trojans as well as spyware downloads. Using a stream-based malware prevention engine, which inspects traffic the moment the first packet is received, the Palo Alto Networks antivirus solution can provide protection for clients without significantly impacting the performance. Best Practices for Ransomware Prevention - Palo Alto Networks The Anti-Virus and Wildfire content contains a list of domains Palo Alto Networks has identified as being potentially associated with malicious traffic; network administrators can block DNS requests to these domains with this profile, or choose to sinkhole the traffic to an internal IP address they have configured for further analysis. types of PA firewall inspection - Palo Alto Networks For example, the Fortigate firewall has 2 inspection modes, the base flow mode and the proxy mode, my question is The Palo Alto firewall, does it also have these types of inspection modes? 0 Likes Share Reply Go to solution MP18 Cyber Elite In response to o_hernandez Options 11-02-2019 08:26 PM


















![FREQUENTLY ASK] Palo Alto Interview Questions and Answers](https://www.acte.in/wp-content/uploads/2021/11/Palo-Alto-Interview-Questions-and-Answers.png)



0 Response to "45 antivirus inspection is proxy based palo alto"
Post a Comment