40 antivirus approaches in network security
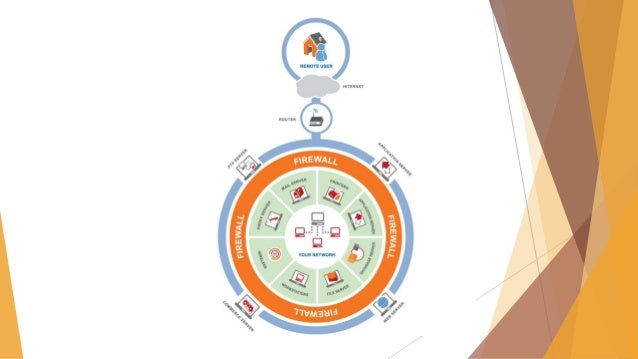
What is Layered Security & How Does it Defend Your Network? Firewall. The first line of defense in your network security, a firewall monitors incoming and outgoing network traffic based on a set of rules. A firewall acts as a barrier between a trusted network and an untrusted network, only allowing into your network traffic that has been defined in the security policy. Patch Management. What Is Network Security | Network Security Solutions | EC-Council Network security is not a destination but a journey. It is a process that strengthens the internal systems with the help of various strategies and activities. These can be grouped into four phases — protect, detect, respond, and predict. Every phase of network security control requires strategies that move the process to the next phase.
Computer Virus Countermeasures - BrainKart The next best approach is to be able to do the following: • Detection: Once the infection has occurred, determine that it has occurred and locate the virus. • Identification: Once detection has been achieved, identify the specific virus that has infected a program. • Removal: Once the specific virus has been identified, remove all traces ...

Antivirus approaches in network security
Advanced Approaches to ATM Network Protection - Security Intelligence Instead, security teams at financial institutions must take a more advanced approach to ATM network protection. ATM security has always been a hot-button issue for banking institutions because ... What is Network Security? - Check Point Software Network Security protects your network and data from breaches, intrusions and other threats. This is a vast and overarching term that describes hardware and software solutions as well as processes or rules and configurations relating to network use, accessibility, and overall threat protection. Network Security involves access control, virus and antivirus software, application security, network analytics, types of network-related security (endpoint, web, wireless), firewalls, VPN encryption ... What is Network Security? | Advantages | Scope & Skill - EDUCBA An Antivirus system is the best example. Furthermore, protection involves protecting data from unauthorized personnel and protection against different activities from employees. These have different types, which include preventive, detective and responsive network security.
Antivirus approaches in network security. Network Security - GeeksforGeeks This is done through Network Access Control which ensures that only a handful of authorized personnel must be able to work with the allowed amount of resources. Antivirus and Anti-malware Software: This type of network security ensures that any malicious software does not enter the network and jeopardize the security of the data. Network Security Devices You Need to Know About An IPS is a network security tool that can not only detect intruders, but also prevent them from successfully launching any known attack. ... Unified threat management (UTM) is an approach to information security in which a single hardware or software installation provides multiple security functions (intrusion prevention, antivirus, content ... Explore 9 essential elements of network security - SearchNetworking UTM devices must include network routing, firewalling, network intrusion prevention and gateway antivirus. They generally offer many other security applications, such as VPN, remote access, URL filtering and quality of service. Approaches to Information Security Implementation In order to ensure the integrity of the security model can be designed using two methods: 1. Bottom-Up Approach: The company's security model is applied by system administrators or people who are working in network security or as cyber-engineers. The main idea behind this approach is for individuals working in this field of information ...
NTS Safeguards Network Security with a Proactive Approach Take a Proactive Approach to Network Security. Protecting your endpoints allows you to proactively identify suspicious devices and isolate them on your network before they can do any damage or access sensitive information. Managed endpoint protection solutions from Network Thinking Solutions are able to quickly detect, analyze, block, and ... Network Security 101 - Definition, Types, Threats, and More A holistic network security strategy consists of a combination of the three network security types: physical, technical, and administrative. In the following subsections, I will go over each one and its conventional components to better illustrate what such an approach entails. Physical Network Security Approaches of Network Security - Bitten Tech Solutions 1.9.2 Layered Security Approach. A layered security approach is one in which not only is the perimeter secured, but individual systems within the network are also secured. All servers, workstations, routers, and hubs within the network are secure. One way to accomplish this is to divide the network into segments and secure each segment as if it ... Common Zero-Day Network Protection Approaches and Drawbacks (Part 1) Common network protection approaches and their limitations Sandboxes - Deployed on top of static code analysis, conventional sandboxes examine the behavior of unknown or... Endpoint security - Serving as a last line of defense, solutions such as EPP s and EDRs inspect an exhaustive number of... ...
What Is Network Security? - Cisco Then you can enforce your security policies. You can block noncompliant endpoint devices or give them only limited access. This process is network access control (NAC). Cisco Identity Services Engine Anti-virus and anti-malware software "Malware," short for "malicious software," includes viruses, worms, Trojans, ransomware, and spyware. Learn about 4 approaches to comprehensive security that help leaders be ... Advantech's security team is now looking to further raise visibility into their IoT and OT risk with agentless, network-layer security provided by Microsoft Defender for IoT—including asset discovery, vulnerability management, and continuous threat monitoring with anomaly detection. "We didn't have staff dedicated to figuring out our ... What is antivirus software (antivirus program)? - Definition from ... Antivirus software, originally designed to detect and remove viruses from computers, can also protect against a wide variety of threats, including other types of malicious software, such as keyloggers, browser hijackers, Trojan horses, worms, rootkits, spyware, adware, botnets and ransomware. How antivirus software works The Fundamentals of Modern Network Security | SentinelOne A modern approach to network security means realising that breaches are sometimes going to happen. The attack surface is so vast that it would be naive to think that your prevention and detection is undefeatable by a determined attacker. Therefore, you need a response plan, aided and abetted by security solutions that can take autonomous action ...
Network Security Threats: 5 Ways to Protect Yourself - The AME Group Use IDS/IPS to track potential packet floods. Use network segmentation. Use a virtual private network (VPN) Conduct proper maintenance. 5. Employee Training. Sometimes external threats are successful because of an insider threat. The weakest link in data protection can be your own employees.
What is Network Security? Defined, Explained, and Explored - Forcepoint Network security is a broad term that covers a multitude of technologies, devices and processes. In its simplest term, it is a set of rules and configurations designed to protect the integrity, confidentiality and accessibility of computer networks and data using both software and hardware technologies. Every organization, regardless of size ...
What is Perimeter Security? | Webopedia Updated on: May 24, 2021. Perimeter security is the protection of a network by monitoring and filtering the traffic that passes through it. A network perimeter refers to the boundary between an organization's network and the other networks it borders (notably the Internet ). A few traditional methods of securing a network perimeter include:
What is Antivirus - Check Point Software Antivirus software is a class of applications that protect computers and remove malicious software or code designed to damage computers or data. Today, malware is evolving so rapidly that some estimate a new malware instance is created nearly every second.
What is Defense in Depth | Benefits of Layered Security | Imperva Broadly speaking, defense-in-depth use cases can be broken down into user protection scenarios and network security scenarios. Website protection. Defense-in-depth user protection involves a combination of security offerings (e.g., WAF, antivirus, antispam software, etc.) and training to block threats and protect critical data.
Two Approaches to Network Security - dummies Choose the closed-door approach only if your network contains a lot of information that is very sensitive, and only if you're willing to invest time administrating your network's security policy. You can think of the open-door approach as an entitlement model, in which the basic assumption is that users are entitled to network access.
How Antivirus Software Works (Detection Science and Mechanism) - MalwareFox In addition to signature detection, antivirus programs also attempt to identify suspicious behavior on a system. This ranges from making suspicious registry entries, or adding items to a list that executes automatically upon system startup. This approach is what helps protect against encrypted viruses, or viruses that are yet to be identified.
Antivirus software - Wikipedia Anti-virus software can attempt to scan for rootkits. A rootkit is a type of malware designed to gain administrative-level control over a computer system without being detected. Rootkits can change how the operating system functions and in some cases can tamper with the anti-virus program and render it ineffective. Rootkits are also difficult to remove, in some cases requiring a complete re-installation of the operating system.
Prevention vs Detection-based Security Approach In a prevention-based strategy, an organization does its best to harden its systems against attack. In a detection-based strategy, a company's security team proactively works to identify and remediate threats that have breached the organization's defenses. Prevention-based security is the more common approach, and, in the past, it was very ...
Antivirus Approaches - Department of Computer Science Antivirus Approaches Antivirus Approaches First-generation A scanner identifies a virus by its bit signature. Assumes that a virus has the same structure and bit pattern in all copies. Maintains a record of the length of the programs and looks for changes in length. Second-generation Uses heuristic rules to search for probable virus infection.
What is Network Security? | Advantages | Scope & Skill - EDUCBA An Antivirus system is the best example. Furthermore, protection involves protecting data from unauthorized personnel and protection against different activities from employees. These have different types, which include preventive, detective and responsive network security.
What is Network Security? - Check Point Software Network Security protects your network and data from breaches, intrusions and other threats. This is a vast and overarching term that describes hardware and software solutions as well as processes or rules and configurations relating to network use, accessibility, and overall threat protection. Network Security involves access control, virus and antivirus software, application security, network analytics, types of network-related security (endpoint, web, wireless), firewalls, VPN encryption ...
Advanced Approaches to ATM Network Protection - Security Intelligence Instead, security teams at financial institutions must take a more advanced approach to ATM network protection. ATM security has always been a hot-button issue for banking institutions because ...





_web(1).jpg)




.jpg.transform/1280w/image.jpg)
0 Response to "40 antivirus approaches in network security"
Post a Comment