39 advanced antivirus techniques in network security
Worry-Free Services Advanced: Cloud-Based ... - Trend Micro Simple. Cloud-based security specifically designed to protect all your devices and email. Stop email threats in the cloud before they reach your network, and protect your devices from spear phishing and advanced targeted attacks. A single, intuitive web console makes managing these powerful capabilities a breeze. Symantec™ Advanced Threat Protection: Network Symantec Advanced Protection: Network also includes Symantec's new Synapse cross-control point correlation capability, which allows security analysts to zero in on the most important incidents. Symantec Cynic™ Cloud-based Sandboxing and Payload Detonation Service
› business-securityBitdefender GravityZone Business Security - SMB Cybersecurity GravityZone Business Security has the industry’s best prevention, detection and blocking capabilities and uses machine learning, advanced heuristics, advanced anti-exploit and other Bitdefender proprietary techniques to protect your endpoints.
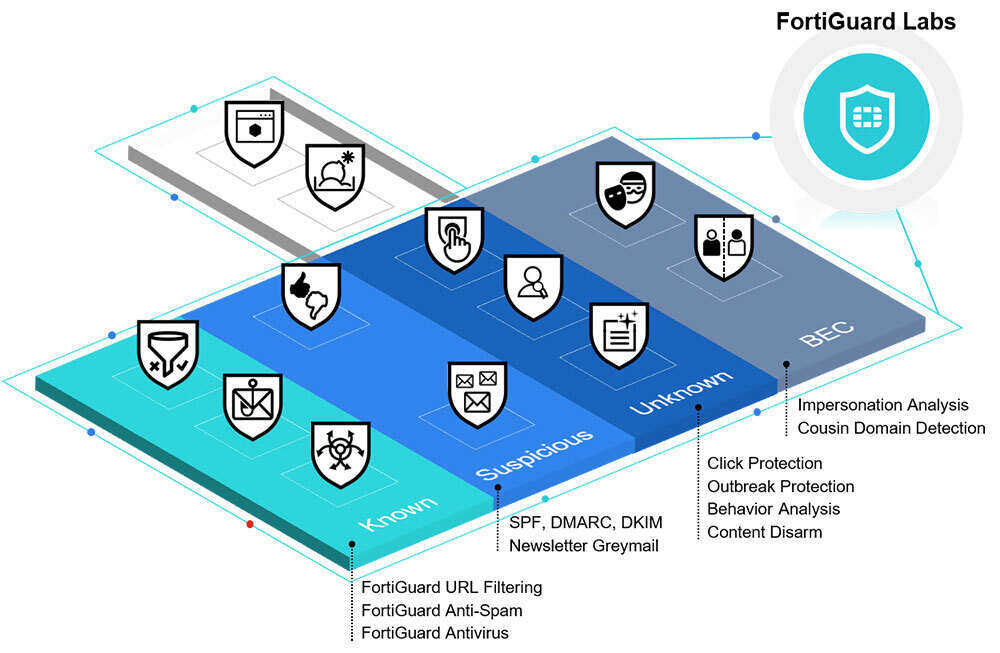
Advanced antivirus techniques in network security
Advanced Endpoint Protection Protects You From Dated ... Seek an advanced security technology for endpoint protection that: Recognizes prevention is the only effective, scalable and sustainable way to reduce the frequency and impact of cyber breaches. Prevents known and unknown malware and zero-day exploits from subverting legitimate applications. What is Bitdefender with Advanced Threat Security (ATS ... Bitdefender ATS, short for Advanced Threat Security, is a modern EPP (endpoint protection) solution that deploys an entire spectrum of technologies to prevent cyberattacks. From authorization checks to machine learning, Bitdefender utilizes industry-leading standards to prevent the execution of attacks on your customer's network and endpoint ... PDF Advanced Cyber Security Techniques - CEMCA Title Advanced Cyber Security Techniques Advisors Mr. R. Thyagarajan, Head, Admn. & Finance and Acting Director, CEMCA Dr. Manas Ranjan Panigrahi, Program Officer (Education), CEMCA Prof. Durgesh Pant, Director-SCS&IT, UOU Editor Mr. Manish Koranga, Senior Consultant, Wipro Technologies, Bangalore Authors
Advanced antivirus techniques in network security. Malware Delivery Campaign Employs Advanced Fileless Techniques "Both the distributed network infrastructure and the advanced fileless techniques allowed this campaign fly under the radar for a while, highlighting how having the right defensive technologies is of utmost importance in order to detect and counter these attacks in a timely manner," Microsoft concludes. PDF Section 4 - Network Security & Advanced Device Techniques NETWORK SECURITY & ADVANCED DEVICE TECHNIQUES Chris Dawe & Tom Bridge. NONE OF THIS SHOULD WORK. ... WIRED EQUIVALENT PRIVACY 64-bit or 128-bit protection ... Section 4 - Network Security & Advanced Device Techniques Created Date: 7/12/2017 2:55:38 PM ... Advanced Approaches to ATM Network Protection An Advanced Approach to ATM Security Security specialists who choose an advanced protection strategy should address all threat types using a security information and event management (SIEM)... The Best Antivirus Protection for 2022 - PCMag Australia The Best Antivirus Protection for 2022 Antivirus software is critical for every PC. Without it, your personal information, your data, and even your bank account are all at risk.
What is Advanced Endpoint Protection (AEP)? | CrowdStrike Advanced endpoint protection (AEP) is a next-generation endpoint security solution that uses artificial intelligence (AI), machine learning (ML) and other intelligent automation capabilities to provide more comprehensive cybersecurity protection from a variety of modern threats, including fileless malware, script-based attacks and zero-day threats. Sophos Endpoint Protection: EPP, EDR, and XDR Explained Sophos exploit prevention is designed to block advanced attack techniques such as fileless, malware-free, and attacks that exploit vulnerabilities. In any given attack chain, only a handful of exploits are used by attackers, and detecting them is the key to effective response. 2021 Intrusion Detection Techniques, Methods & Best ... Network-based intrusion detection techniques expand the scope of coverage still further to all devices on a network or subnetwork (sometimes, multiple instances of solutions collaborate to accomplish this, due to the volume of traffic). Because they are the most general, they sometimes miss problems the other two might detect. › best-antivirus-softwareBest Antivirus Software 2022 | Top Ten Reviews Mar 11, 2022 · A firewall is a network security device on your computer that monitors incoming and outgoing network traffic, and blocks unauthorized or dangerous traffic. Windows and Mac computers have built-in firewalls, but many antivirus programs come with their own firewall program too. VPN VPN stands for virtual private network.
What Is Network Security | Network Security Solutions | EC ... The safety of data is only made possible by implementing useful network security tools and techniques. The importance of network security in the modern business atmosphere has increased after a major portion of the workforce went remote due to COVID-19. Today, the office system is distributed in one huge network across multiple locations. › en-us › productsServer Security: Sophos Intercept X for Server with EDR Intercept X Advanced for Server with XDR is the industry’s only XDR solution that synchronizes native endpoint, server, firewall, email, cloud and O365 security. Get a holistic view of your organization’s environment with the richest data set and deep analysis for threat detection, investigation and response for both dedicated SOC teams and ... Advanced Threat Prevention - Palo Alto Networks Best In Class IPS. Decrease your risk and cost of poorly integrated network threat prevention. Integrated on the ML-powered NGFW, Advanced Threat Prevention provides thorough protection against a wide variety of exploits while reducing the need for standalone IPS solutions. Download datasheet. Bypass Antivirus with Advanced Exploitation Frameworks Bypass Antivirus with Advanced Exploitation Frameworks Malicious Payload Evasion Techniques with Advanced Exploitation Frameworks Sophisticated threats are Evolving with much more advanced capabilities and giving more pain for analysis even evade the advanced security software such as Antivirus.
Combating Advanced Evasion Techniques with Network ... Testing the effectiveness of Network Security Platform against advanced evasion techniques You can use an advanced evasion technique testing tool to test the effectiveness of McAfee Network Security Platform against advanced evasion techniques. For this article, we show this test using McAfee (Stonesoft) Evader.
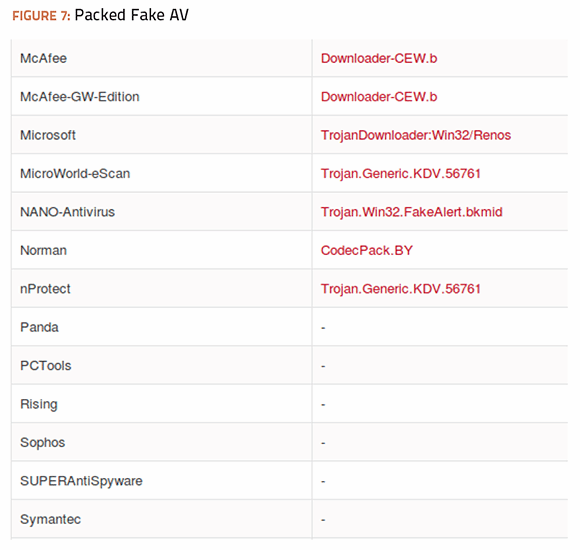
Advanced antivirus evasion techniques | Semantic Scholar Advanced antivirus evasion techniques | Semantic Scholar In this thesis we examine the use of Return-Oriented Programming (ROP) combined with other practices for local (i.e. infected executables on disk) antivirus evasion. ROP is considered as a polymorphism alternative to crypters and packers.
PDF And Advanced Techniques to Safeguard Your Data Cybersecurity and Advanced Techniques to Safeguard Your Data PURE Insurance PASSWORD SUBMIT Must be 8 characters or more and include a capital letter, a symbol (*&%!#$ etc.) and a number. 7 1,220,523 Phishing attacks in 2016ii NO. 2 Fighting Email Fraud Avoid becoming a victim of malicious emails.
PDF CTS 2317 Advanced Network Security - Miami Dade College 4. Describing the security capabilities of information systems, including memory protection, Trusted Platform Module (TPM), encryption and decryption. 5. Describing methods to assess and mitigate the vulnerabilities of security architectures, designs, and solution elements, including: client-based and server-based systems, databases,
Advanced Threat and Network Analysis: Your Security Secret ... Today, blocking the latest exploits requires a combination of advanced threat and network protection techniques that help you predict and influence outcomes, not merely react. Learn more about the specific technologies being used to prevent, detect and eliminate advanced threats at ESET's next webinar. Topics include:
What is advanced evasion technique (AET)? - Definition ... An advanced evasion technique (AET) is a type of network attack that combines several different known evasion methods to create a new technique that's delivered over several layers of the network simultaneously.
Applied Network Security [Book] - oreilly.com About This Book Deep dive into the advanced network security attacks and techniques by leveraging tools such as Kali Linux 2, MetaSploit, Nmap, and Wireshark Become an expert in cracking WiFi passwords, penetrating anti-virus networks, sniffing the network, and USB hacks
Comodo Cleaning Essentials | Malware Removal Tool 2022 Perfect for ensuring network endpoints are totally clean of threats; No installation required – can run direct from USB or user desktop via RDP ; What is Comodo Cleaning Essentials? Comodo Cleaning Essentials (CCE) is a set of powerful security tools designed to help users identify and remove malware and unsafe processes from Windows computers. Designed as a portable …
Improve Network Security with Advanced Threat Protection ... It uses machine learning to identify and protect against advanced threats. ATP enhances the protection of standard tools by providing advanced malware analysis of artifacts traversing the data center. Other malware detection technologies inspect content and identify potentially malicious code, but they cannot interact with malware.
› uscert › ncasTactics, Techniques, and Procedures of Indicted APT40 Actors ... Jul 19, 2021 · APT40 has used a variety of tactics and techniques and a large library of custom and open-source malware—much of which is shared with multiple other suspected Chinese groups—to establish initial access via user and administrator credentials, enable lateral movement once inside the network, and locate high value assets in order to exfiltrate ...
PDF IT-2710: Advanced Topics in Network Security Objective(s): 1. Implement Authentication, Authorization, and Accounting (AAA). 2. Mitigate threats to networks using Access Controls. 3. Demonstrate methods used to implement secure network design, management, and reporting. 4. Mitigate common attacks. 5. Explain the Incident Response Process. 6.
What is Endpoint Security? - CrowdStrike Antivirus is often part of an endpoint security solution and is generally regarded as one of the more basic forms of endpoint protection. Instead of using advanced techniques and practices, such as threat hunting and endpoint detection and response (EDR), antivirus simply finds and removes known viruses and other types of malware .
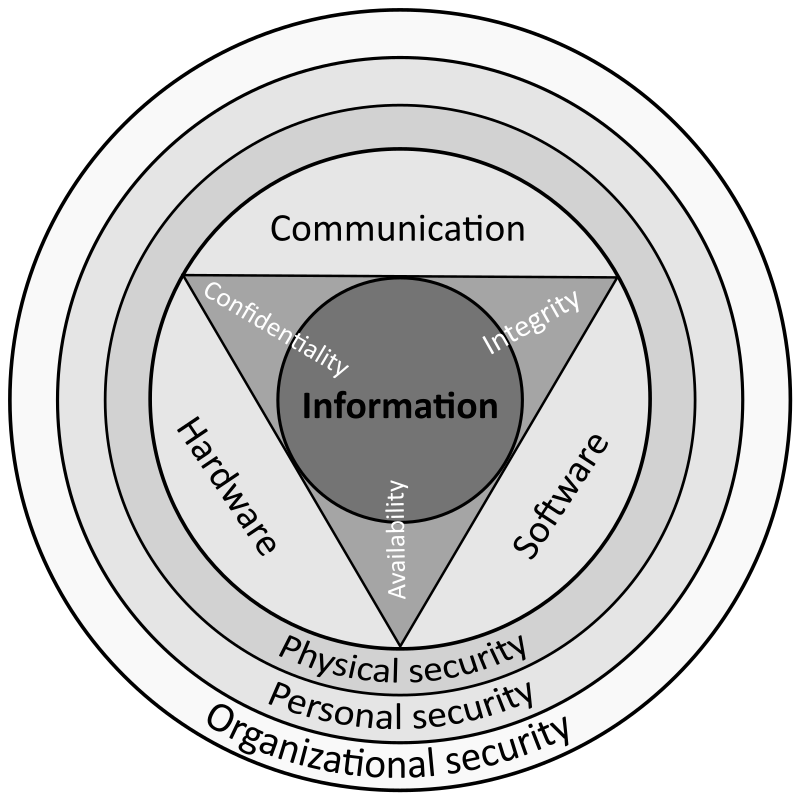
PDF Network Security - Tutorialspoint Network Security 6 Goals of Network Security As discussed in earlier sections, there exists large number of vulnerabilities in the network. Thus, during transmission, data is highly vulnerable to attacks. An attacker can target the communication channel, obtain the data, and read the same or re-insert a false message to achieve his nefarious aims.
ESET Endpoint Protection Advanced: Quick Solution Overview ESET Endpoint Antivirus uses Advanced Memory Scanner, a proprietary technology, to help solve this challenge. The scanner proactively looks for fileless malware behavior and can stop threats according to actions taken by computer processes when the malware decloaks in memory. Obfuscated malware
› int › homeInternet Security with antivirus protection | ESET Advanced protection against all kinds of threats ESET INTERNET SECURITY EDITION 2022 Ideal for modern users concerned about their privacy, who actively use internet for shopping, banking, work and communication.
Advanced Network Security (CS4155) - Cyber Threat Intelligence In CS4155 Advanced Network Security, students get in addition to the theory also the opportunity for studying vulnerabilities and countermeasures in networking systems and communication protocols in detail, including in-depth study of protocol security analysis as well as a handson implementation of defense mechanisms on actual systems.
Foundational Security VS Advanced Cybersecurity-Corsica ... Use an enterprise-class firewall device to secure your network and keep out unwanted and unsafe traffic. Make sure it provides visibility into any intrusion attempts and gives you the ability to block access to undesirable websites and applications. Also make sure it supports remote-access VPN to securely accommodate your offsite employees.
How to use Network Security Platform to combat Advanced ... An AET combines several known evasion methods to create a new technique that is delivered over multiple network layers simultaneously. A few examples of such advanced evasions are: SMB or MSRPC fragmentation SMB padding Application layer evasion through document obfuscation JavaScript obfuscation HTTP UTF-8 encoded content
› en_us › businessAdvanced Threat Protection | High Detection Rate, Sandbox ... Advanced sandbox analysis. Deep Discovery Analyzer provides custom sandbox analysis to extend the value of security products, such as endpoint protection, web and email gateways, network security, and other Deep Discovery offerings. Suspicious objects or URLs are automatically or manually sent for analysis, and threat insight is automatically ...
PDF Advanced Cyber Security Techniques - CEMCA Title Advanced Cyber Security Techniques Advisors Mr. R. Thyagarajan, Head, Admn. & Finance and Acting Director, CEMCA Dr. Manas Ranjan Panigrahi, Program Officer (Education), CEMCA Prof. Durgesh Pant, Director-SCS&IT, UOU Editor Mr. Manish Koranga, Senior Consultant, Wipro Technologies, Bangalore Authors
What is Bitdefender with Advanced Threat Security (ATS ... Bitdefender ATS, short for Advanced Threat Security, is a modern EPP (endpoint protection) solution that deploys an entire spectrum of technologies to prevent cyberattacks. From authorization checks to machine learning, Bitdefender utilizes industry-leading standards to prevent the execution of attacks on your customer's network and endpoint ...
Advanced Endpoint Protection Protects You From Dated ... Seek an advanced security technology for endpoint protection that: Recognizes prevention is the only effective, scalable and sustainable way to reduce the frequency and impact of cyber breaches. Prevents known and unknown malware and zero-day exploits from subverting legitimate applications.







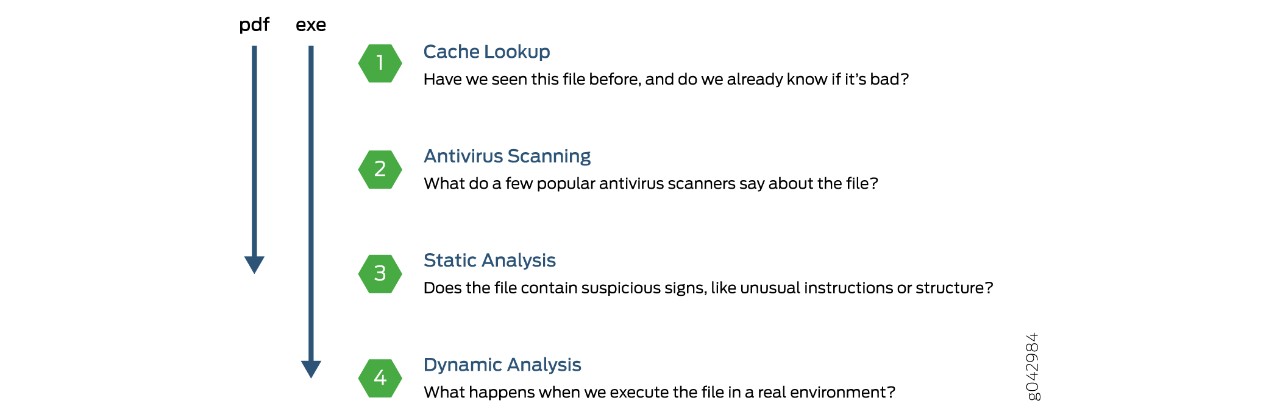



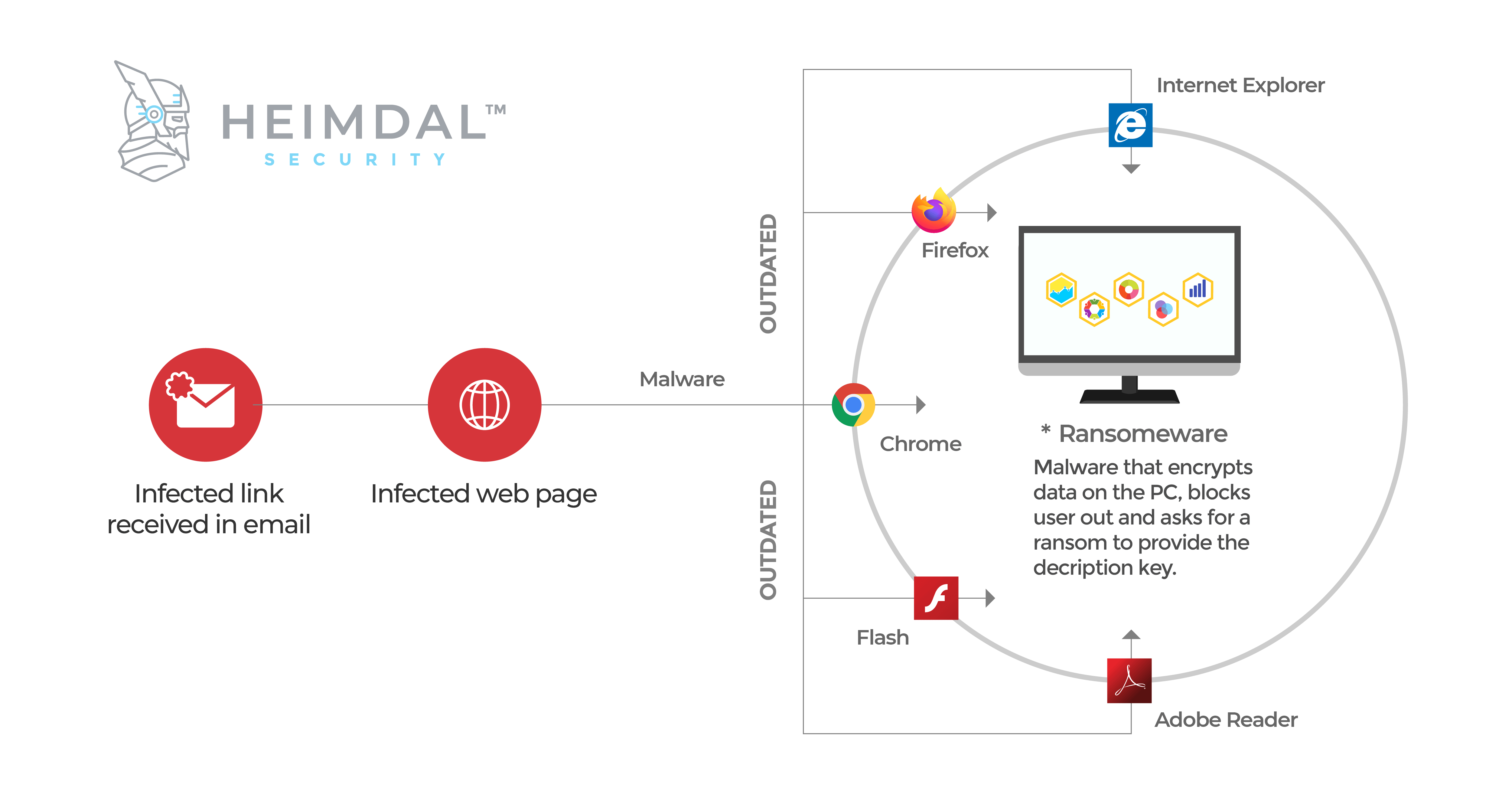

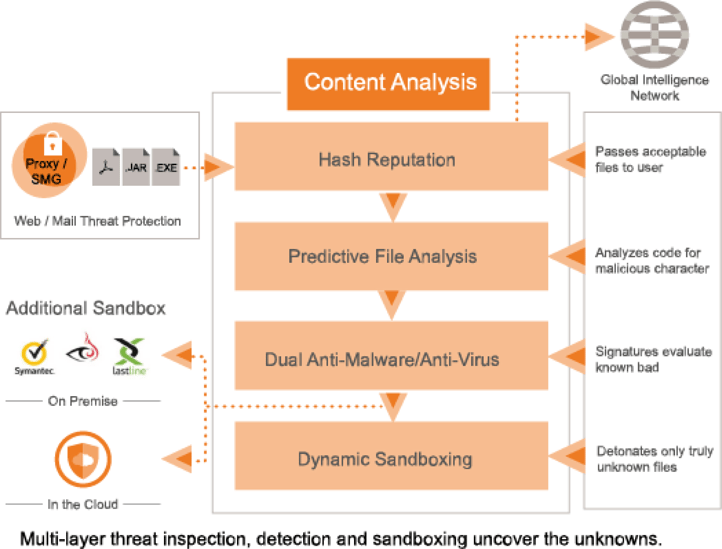









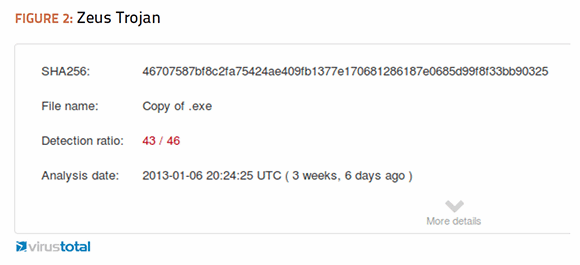

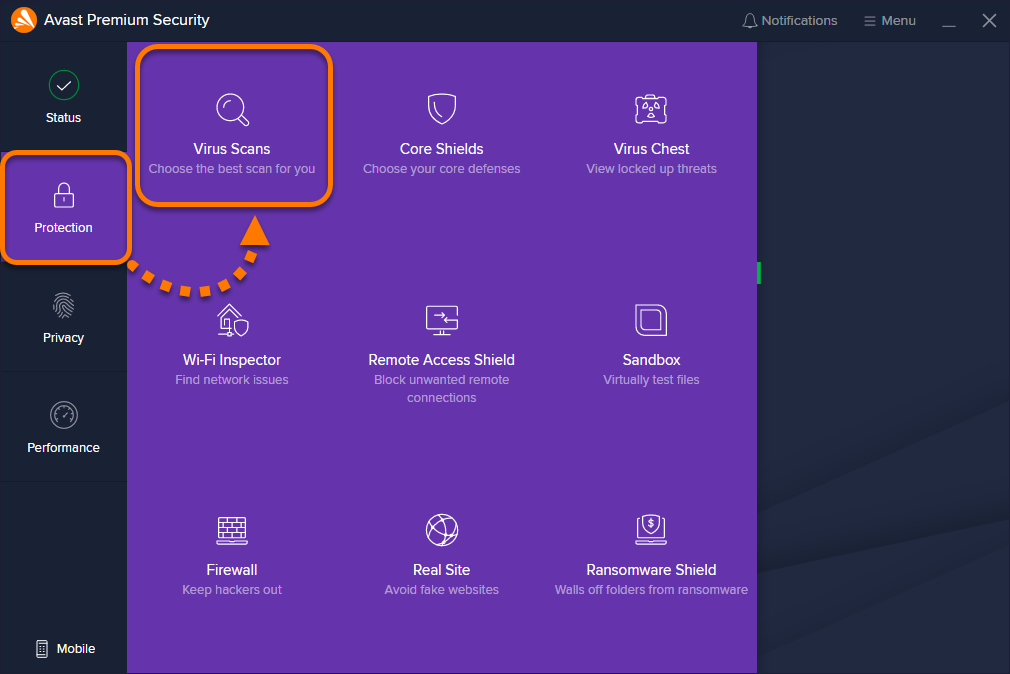






0 Response to "39 advanced antivirus techniques in network security"
Post a Comment